Prepare the security check environment for Rails 6
Purpose of this article
Visualize security measures in Rails We have built a mechanism to detect any security vulnerabilities. I hope it will be helpful for those who have trouble with the memorandum and Rails security measures. I wrote this article.
Construction environment
- Rails: 6.0.3.3
- Ruby: 2.6.6
Gem
- Brakeman
- bundler-audit
About Gem to use
Brakeman
Official site: https://brakemanscanner.org/

A library that can detect security vulnerabilities such as SQL injection, XSS, and Dos attacks. There are more than 50 types of analysis items, which are also used on GitHub, Twitter, etc. We recommend using it as a code security measure for Rails.
・ Installation method
It's easy to install with bundler in your Rails project.
Add gem under develop environment and install by bundle.
group :development do
gem 'brakeman'
end
Easy to install globally.
gem install brakeman
·Execution method
It's easy to do.
Just run the brakeman command under the Rails environment and it will start running.
The sample below is taken from the execution result of my application development environment.
My app is a Docker-compose environment
Running after docker-compose exec web bash.
When the execution starts, the report will be output as shown below.
❯ docker-compose exec web bash
root@3dde8034237f:~# brakeman
Loading scanner...
Processing application in /app
Processing gems...
[Notice] Detected Rails 6 application
Processing configuration...
[Notice] Escaping HTML by default
Parsing files...
Processing initializers...
Processing libs...ed
Processing routes...
Processing templates...
Processing data flow in templates...
Processing models...
Processing controllers...
Processing data flow in controllers...
Indexing call sites...
Running checks in parallel...
- CheckBasicAuth
- CheckBasicAuthTimingAttack
- CheckCrossSiteScripting
- CheckContentTag
- CheckCookieSerialization
- CheckCreateWith
- CheckCSRFTokenForgeryCVE
- CheckDefaultRoutes
- CheckDeserialize
- CheckDetailedExceptions
- CheckDigestDoS
- CheckDynamicFinders
- CheckEscapeFunction
- CheckEvaluation
- CheckExecute
- CheckFileAccess
- CheckFileDisclosure
- CheckFilterSkipping
- CheckForgerySetting
- CheckHeaderDoS
- CheckI18nXSS
- CheckJRubyXML
- CheckJSONEncoding
- CheckJSONEntityEscape
- CheckJSONParsing
- CheckLinkTo
- CheckLinkToHref
- CheckMailTo
- CheckMassAssignment
- CheckMimeTypeDoS
- CheckModelAttrAccessible
- CheckModelAttributes
- CheckModelSerialize
- CheckNestedAttributes
- CheckNestedAttributesBypass
- CheckNumberToCurrency
- CheckPageCachingCVE
- CheckPermitAttributes
- CheckQuoteTableName
- CheckRedirect
- CheckRegexDoS
- CheckRender
- CheckRenderDoS
- CheckRenderInline
- CheckResponseSplitting
- CheckRouteDoS
- CheckSafeBufferManipulation
- CheckSanitizeMethods
- CheckSelectTag
- CheckSelectVulnerability
- CheckSend
- CheckSendFile
- CheckSessionManipulation
- CheckSessionSettings
- CheckSimpleFormat
- CheckSingleQuotes
- CheckSkipBeforeFilter
- CheckSprocketsPathTraversal
- CheckSQL
- CheckSQLCVEs
- CheckSSLVerify
- CheckStripTags
- CheckSymbolDoSCVE
- CheckTemplateInjection
- CheckTranslateBug
- CheckUnsafeReflection
- CheckValidationRegex
- CheckWithoutProtection
- CheckXMLDoS
- CheckYAMLParsing
Checks finished, collecting results...
Generating report...
== Brakeman Report ==
Application Path: /app
Rails Version: 6.0.3.3
Brakeman Version: 4.9.1
Scan Date: 2020-09-15 02:51:42 +0000
Duration: 2.0712347 seconds
Checks Run: BasicAuth, BasicAuthTimingAttack, CSRFTokenForgeryCVE, ContentTag, CookieSerialization, CreateWith, CrossSiteScripting, DefaultRoutes, Deserialize, DetailedExceptions, DigestDoS, DynamicFinders, EscapeFunction, Evaluation, Execute, FileAccess, FileDisclosure, FilterSkipping, ForgerySetting, HeaderDoS, I18nXSS, JRubyXML, JSONEncoding, JSONEntityEscape, JSONParsing, LinkTo, LinkToHref, MailTo, MassAssignment, MimeTypeDoS, ModelAttrAccessible, ModelAttributes, ModelSerialize, NestedAttributes, NestedAttributesBypass, NumberToCurrency, PageCachingCVE, PermitAttributes, QuoteTableName, Redirect, RegexDoS, Render, RenderDoS, RenderInline, ResponseSplitting, RouteDoS, SQL, SQLCVEs, SSLVerify, SafeBufferManipulation, SanitizeMethods, SelectTag, SelectVulnerability, Send, SendFile, SessionManipulation, SessionSettings, SimpleFormat, SingleQuotes, SkipBeforeFilter, SprocketsPathTraversal, StripTags, SymbolDoSCVE, TemplateInjection, TranslateBug, UnsafeReflection, ValidationRegex, WithoutProtection, XMLDoS, YAMLParsing
== Overview ==
Controllers: 11
Models: 6
Templates: 56
Errors: 0
Security Warnings: 0
== Warning Types ==
No warnings found
(END)
A long report is output as above.
The output message below the last Warning Types
If it says No warnings found, it's OK.
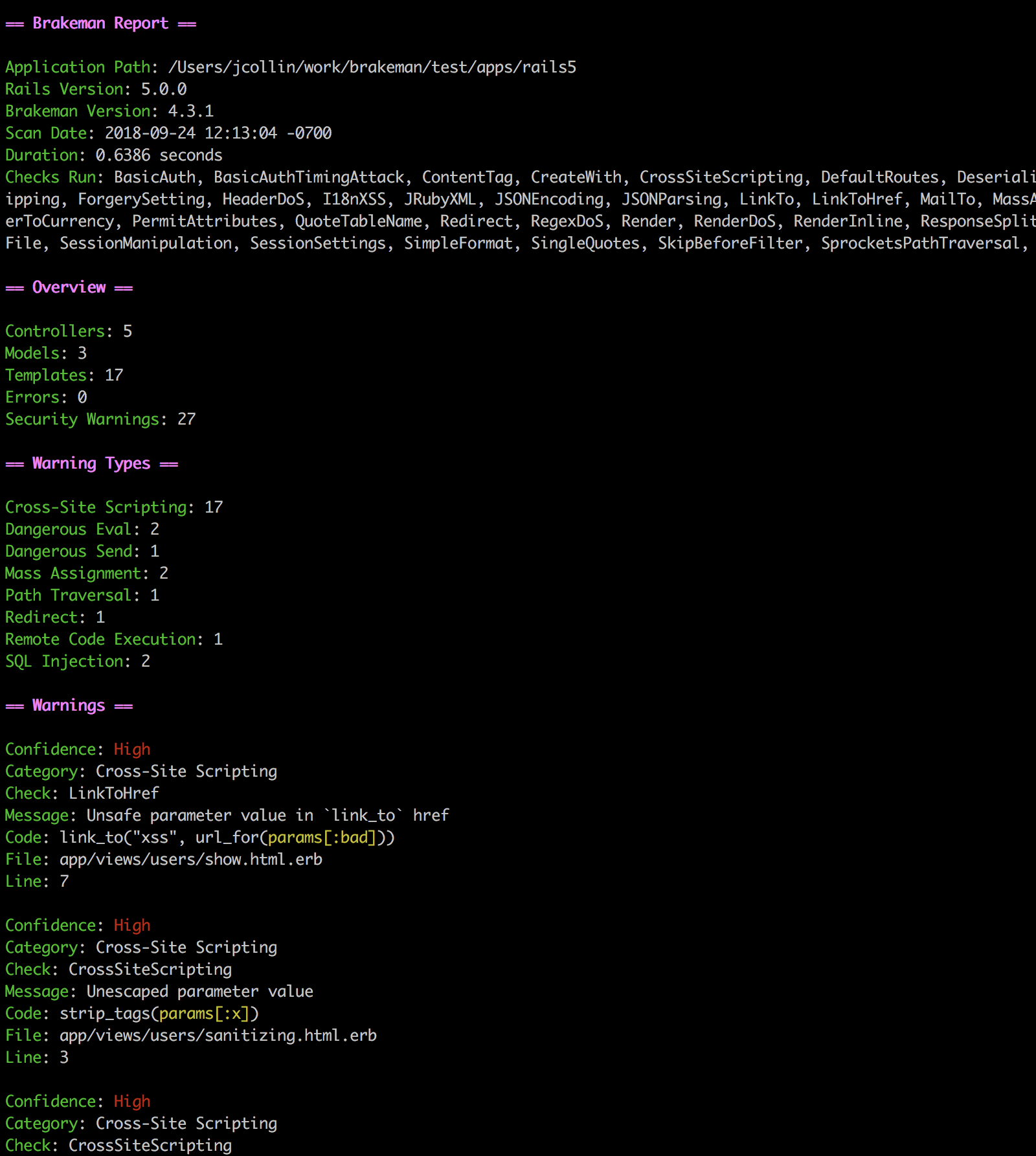
By the way, if a warning occurs, it will be as follows. (The following is a quote from the official website Quick Start.) XSS warning.
When a warning occurs, it is necessary to read the content and take action.
・ Https://brakemanscanner.org/docs/quickstart/
In addition, Brakeman can set the warning output level in 3 steps. The README on GitHub has the following explanation.
High - Either this is a simple warning (boolean value) or user input is very likely being used in unsafe ways. Medium - This generally indicates an unsafe use of a variable, but the variable may or may not be user input. Weak - Typically means user input was indirectly used in a potentially unsafe manner.
Translated in Japanese
- High
Whether it's a simple warning (boolean) or the user input is likely to be used in an insecure way
a level that needs to be addressed - Medium
It generally indicates unsafe use of variables, but variables may or may not be user-input, so check the content and take action. - Weak
In general, it means that the user's input was used in a way that may indirectly be insecure.
You should check the usage and settings.
The above level can be set with w1-w3 and output. w1 is the lowest level and w3 is the highest level. For example, w3 gives the following command. If you want to enter with CI settings, w2 etc. may be good.
brakeman -w3
Now you're ready to security check your Rails code.
Bundler-audit
https://github.com/rubysec/bundler-audit

- The image is a bundler image.
A tool for detecting vulnerabilities in Gemfile.lock. You can detect unsafe gems. Installation in combination with Brakeman is recommended.
・ Installation method
Like Brakeman, add it to the Gemfile and bundle it.
group :development do
gem 'bundler-audit'
end
·Execution method
Execute it with the following command.
bundle-audit
--If there is no vulnerability
root@3dde8034237f:~# bundler-audit
No vulnerabilities found
--If there is a vulnerability
The example below shows that actionpack version 3.2.10 is vulnerable. Also, as a solution, Solution: upgrade to ~> 2.3.15, ~> 3.0.19, ~> 3.1.10,> = 3.2.11 A version change is shown. If any vulnerabilities are shown, please perform the version correction work.
Name: actionpack
Version: 3.2.10
Advisory: OSVDB-89026
Criticality: High
URL: http://osvdb.org/show/osvdb/89026
Title: Ruby on Rails params_parser.rb Action Pack Type Casting Parameter Parsing Remote Code Execution
Solution: upgrade to ~> 2.3.15, ~> 3.0.19, ~> 3.1.10, >= 3.2.11
In addition, work that updates the Gemfile occurs, if it occurs, execute it as follows. The following is recommended on the official website even when using it in CI. bundler-audit makes all security recommendations related to Ruby libraries I'm using ruby-advisory-db, which is used to compile. This command updates ruby-advisory-db and then checks it.
bundle-audit check --update
Now you are ready to check for Gem vulnerabilities.
Afterword
Security measures require a wide variety of checks, from SQL and XSS measures to Dos attacks. In addition to code security measures I have to find vulnerabilities in the Gem I'm using I think it could be the target of attacks using that vulnerability.
The library introduced this time is code and Gem I think it is an effective means for implementing and visualizing security measures on both sides. I hope it will be helpful for those who develop Rails.
- Addition We have not introduced security measures on the infrastructure side this time. Not only Rails side but also Rails side security measures for apps in general I think that the infrastructure side (in AWS, IAM and VPC settings, encryption) etc. are required.
Recommended Posts